Analysis
All the analyses performed by Cosmo during a scan are detailed below.
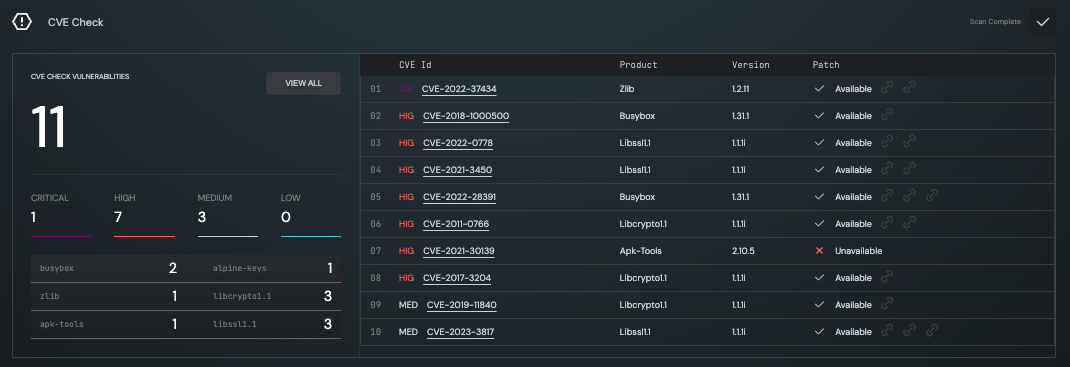
CVE Check
The CVE Check Analysis identifies known vulnerabilities in open source components found in your firmware, categorised by severity. For each CVE, Cosmo gives you information about its remediation instructions.
Password Hash
The Password hash analysis looks for hard-coded weak passwords in your firmware.
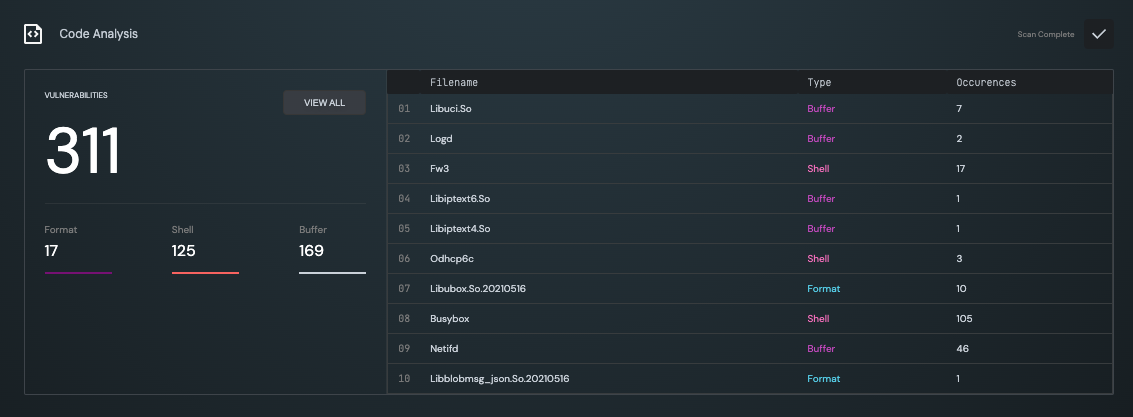
Code Analysis
The Code Analysis looks for potential buffer overflow or command injection vulnerabilities inside your firmware binary executables.
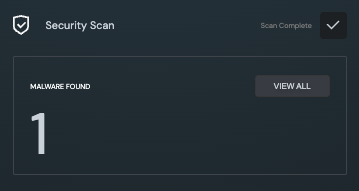
Security Scan
The Security Scan analysis looks for known malicious files (such as malware, trojan, etc.) within the file system.
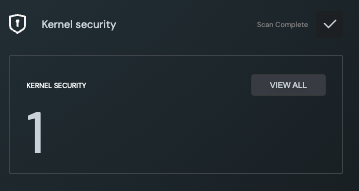
Kernel Security
The Kernel Security analysis looks for third-party kernel security modules installed in the firmware. These modules provide additional security directly at kernel level and having even at least one of them in place is considered good practice from a security standpoint.
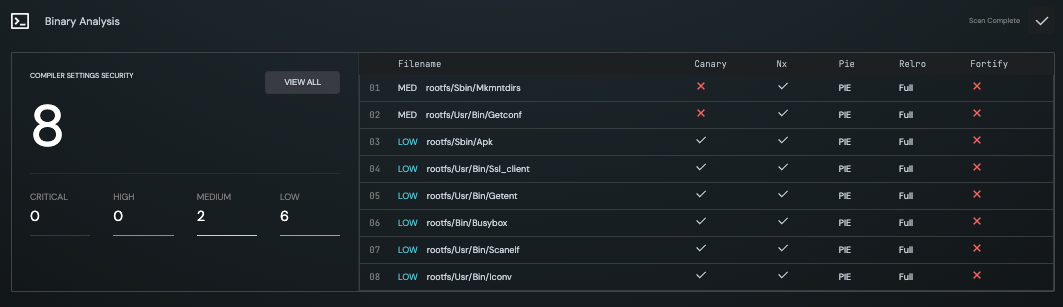
Binary Analysis
The Binary Analysis checks that the compiler settings for all executables conform to secure coding practices (i.e. Stack Canaries, etc.).
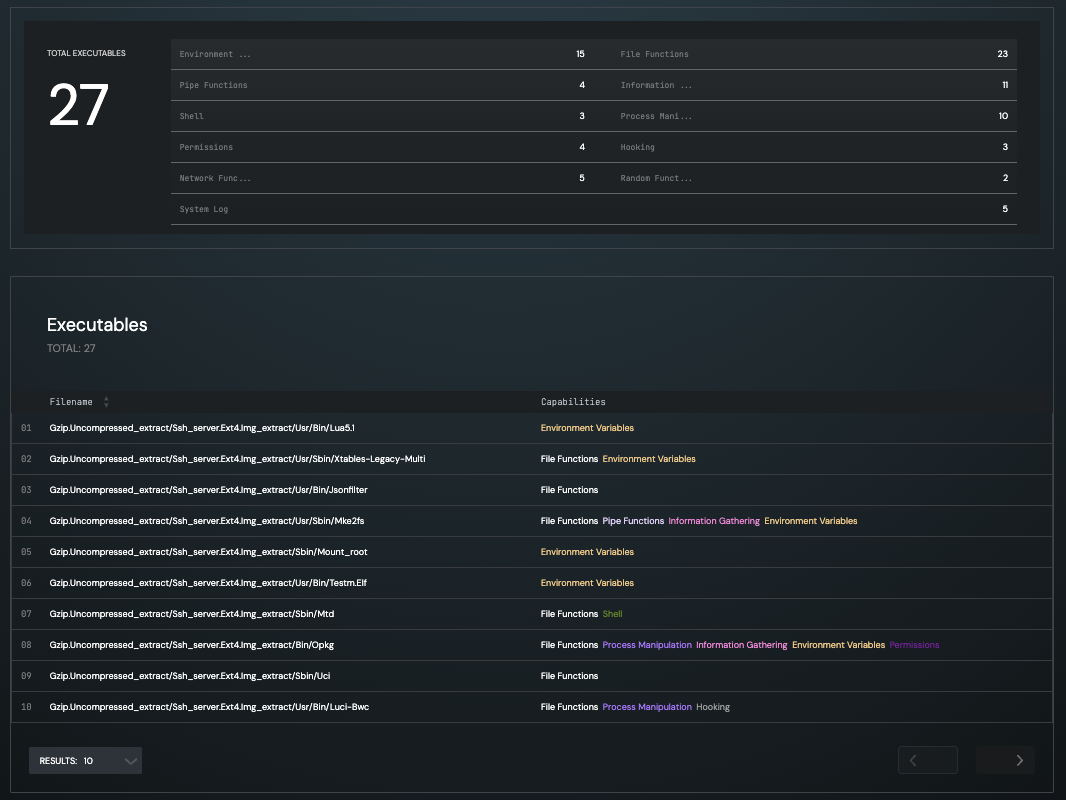
Capabilities Analysis
The Capabilities Analysis determines the capabilities for each function defined in the executable.